Blue Prism application server
Blue Prism application servers should not be installed on any domain or network where there is internet facing access. The Blue Prism platform should be implemented into your environment as a separate entity. This can be achieved through network segregation, for example, using jump servers for cross-domain travel, or other similar methods. It is advised that you also consult the Robotic Operating Model (ROM) Security information on the Blue Prism Portal for recommendations of best practice.
Install and configure the first application server. Includes configuring a new Blue Prism database or connecting to a pre-configured database.
Steps
Run the appropriate installer depending on whether you wish to use the 32-bit or 64-bit installer.
- 32-bit Installer: BluePrismx.x.nn_x86.msi
- 64-bit Installer: BluePrismx.x.nn_x64.msi
Installers are available from the Blue Prism Portal.
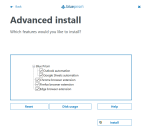
Advanced install options
The following additional components are available during a Blue Prism installation if the Advanced install check box is enabled on the Install location screen:
- Outlook automation – Required on devices where the Blue Prism MS Outlook Email VBO will be executed.
- Google Sheets automation – Required on devices where the Blue Prism Google Sheets VBO will be executed
- Chrome browser extension – Required on devices that will be used to automate Chrome.
- Firefox browser extension – Required on devices that will be used to automate Firefox.
-
Edge browser extension – Required on devices that will be used to automate Chromium-based Edge.
All components are installed by default unless they are deselected before proceeding with the installation.
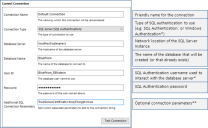
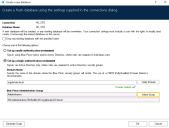
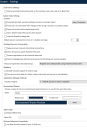
When Blue Prism is launched for the first time it is necessary to define a connection to the SQL Server instance where the database is, or will be, hosted.
-
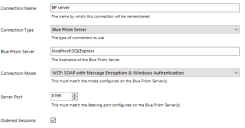
Click Configure connection. This will open the Connection Configuration dialog where users can provide the connection information.
-
Specify the name for this connection, and the settings required to connect to the SQL Server instance.
The name of the intended database will also be specified on this screen. This is the name that will be used to create a new database; or it can be the name of an existing database.
*If the Connection type applies Windows Authentication, the context of the user currently logged into the device will be used to authenticate against the SQL Server. Where possible Windows Authentication (rather than SQL Authentication) should be used.
- SQL Authentication – Connection Name (must be unique), Database Server, Database Name, User ID
- Windows Authentication – Connection Name (must be unique), Database Server, Database Name
- Availability Group (SQL Authentication) – Connection Name (must be unique), Database Server, Database Name, User ID
- Availability Group (Windows Authentication) – Connection Name (must be unique), Database Server, Database Name
** Can be left blank. Populate if there is a requirement to add custom SQL Connection Parameters such as: encrypt=true; trustservercertificate=true.
See SQL Server Connection Properties information provided by Microsoft for a list of available values.
If connecting to Microsoft SQL Azure, the database must be pre-existing, and the connection details provided within the Azure database configuration area should be used. Example settings (ADO.NET) are provided below:
Connection Type
SQL Server (SQL Authentication)
Database Server:
e12n3456.database.windows.net,1433
Database Name:
BluePrism
User ID:
authUser@e12n3456
Password:
*********
-
Click Test Connection to establish if a connection can be established with the SQL Server.
As the database does not yet exist we expect to be presented with a meaningful error.
Expected Responses
Database 'Blue Prism' does not exist.
This does not appear to be a valid Blue Prism database.
The database needs configuring before it can be used.
Indicates that a successful connection was established with the server, but that the database does not yet exist.
Indicates that a successful connection was established with the server, but that it cannot be verified as a Blue Prism database. This would typically be the case where the database has been manually created but has not had the Blue Prism schema applied.
Indicates that a successful connection was established with the server, and that a Blue Prism database has been found, but that some further configuration is required.
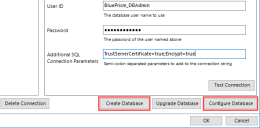
Click OK to clear the message and then click Create Database.
Click OK to clear the message and then click Configure Database.
Proceed to the next step for further instructions.
Alternative Responses
Database Valid
Unable to determine whether database exists – A network-related or instance-specific error occurred whilst establishing a connection to SQL Server. The server was not found or was not accessible. Verify that the instance name is correct and that SQL Server is configured to allow remote connections. (provider: Named Pipes Provider, error: 40 – Could not open a connection to SQL Server)
Indicates that a successful connection was established with the server and the database.
Actions to Create or Configure the database can be bypassed.
Indicates that an error occurred establishing a connection with the SQL Server. Check that the details for the SQL Server instance are correct, and refer to the Troubleshooting an installation.
There are three stages involved in the creation and preparation of a database for use with Blue Prism.
- Create a SQL Server database – This can either be achieved manually or by using the in-product Create Database action.
- Apply Blue Prism schema – The database schema is applied to the configured database.
- The in-product Create Database action will automatically apply the schema to a database that it creates; or to a specifiable pre-existing blank database.
- Alternatively, the schema can be applied by manually using the CreateScript.sql against a pre-existing database. The CreateScript.sql can be obtained via request from Blue Prism Customer Support or generated using the Blue Prism client – Click Generate Script at the bottom of the Create a new database or Upgrade the database screens.
-
Configure Blue Prism sign-on settings – A number of configuration options are applied to the database. These are applied automatically when using the in-product Create Database action. If the database has been created and had the schema applied manually the Configure Database action must be used.
All of the above stages are completed in a single step when using the in-product Create Database functionality.
-
To launch the in-product utility to create and configure a database, use the Create Database or Configure Database options in the Connection Configuration dialog.
-
In the Create a new database dialog, select whether to drop and recreate the database if already exists.
- Select the preferred authentication method for users connecting to Blue Prism. You can choose between two types of environments:
- Multi-authentication environment – this environment supports both Blue Prism native authentication and Active Directory authentication where roles are mapped to individual users in Blue Prism. When creating new users in a multi-authentication environment, administrators can select to create either a single Blue Prism native user, or one or more Active Directory users. The authentication type is configured as part of the user creation and cannot be changed later.
- Single-authentication environment – referred to as Active Directory Single Sign-On in previous versions of Blue Prism, this environment supports Active Directory authentication where users log in via Active Directory only and roles are mapped to Active Directory security groups. To set up a single-authentication environment, it is necessary to enter the name of the domain that contains the Active Directory security groups that are to be associated with security roles in Blue Prism, and to select the security group within that domain whose members will be granted system administrator access to Blue Prism.
- Only custom security groups should be associated with Blue Prism – do not use built-in groups, or groups with derived membership.
- Click OK to complete the database configuration.
Support for contained databases
Blue Prism supports the use of contained databases, hosted on Microsoft SQL Server. To use a contained database, it is necessary to manually create the database and apply the Blue Prism CreateScript.sql.
For more information, see Contained databases.
It is now possible to log in for the first time and carry out some system-wide configuration.
The steps will differ slightly depending on whether the environment is configured to use Blue Prism native authentication or Active Directory authentication.
Blue Prism native authentication
Log in using the default credentials:
- Username: admin
- Password: admin
Follow the onscreen instructions to change the administrator password.
This video shows you how to recover your admin password.
Active Directory authentication in a single-authentication environment
Log in by clicking Sign in to validate that the configuration has been correctly applied.
Active Directory authentication in a multi-authentication environment
You will first have to log in using Blue Prism native authentication before setting up users for Active Directory authentication in a multi-authentication environment.
See Single sign-onfor more details.
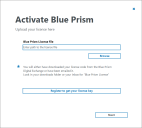
A valid license file is required to activate the software. License files can be obtained from a Blue Prism Account Manager.
After logging in, if a license is not already installed or the current one has expired, you will be prompted to enter your license key.
Licenses are managed in Blue Prism in the System settings – click the System tab and select System > License from the navigation tree.
Details of the active license are displayed and options are available to install new licenses and remove existing ones. Select the Show expired licenses checkbox to display details of licenses that have reached their expiry date.
Click Install new licence to add a license.
In order to support the use of Credential Manager (for securely storing credentials), configure the encryption scheme that will be used.
- Click the System tab and select Security > Encryption Schemes from the navigation tree.
- Select the scheme listed and click Edit.
-
Follow the steps below as appropriate:
It is not recommended practice for enterprise customers operating at scale to store the encryption scheme keys in the database.
Standalone Deployment
Multiple Component (App Server) Deployment
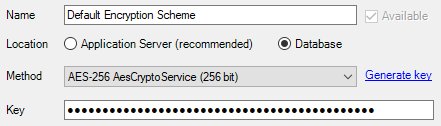
- Select Database.
- Select AES-256.
- Click Generate Key.
- Click OK.
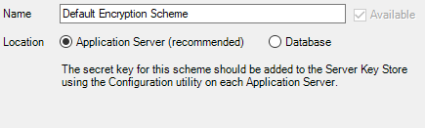
- Select Application Server.
- Click OK.
A copy of each key must be backed up in a secure location.
A number of optional settings are commonly applied. These can be found under System > Settings on the System tab.
For more information, see System settings.
|
Setting |
Information |
|---|---|
|
Start a personal runtime resource on this machine |
Commonly disabled on all devices except for standalone deployments of Blue Prism, provides a local runtime resource when a user logs into Blue Prism. |
|
Automatically back up when editing a process or business object |
Indicates the frequency at which auto-save will run. Commonly this settings is only adjusted in environments operating over high-latency networks. |
|
Force users to summarize their changes |
Requires users to add a comment when making changes to these records. |
|
Password controls allow pasted passwords |
When enabled, users can paste into password controls within the Blue Prism interface. Disable this setting to require users to type (rather than paste) passwords and to increase the security of typed values in memory. |
|
Allow latest runtime resource screen capture |
Enabled by default. Indicates whether a user can configure an exception stage to capture and store an image of the screen when an error occurs. The latest screen capture for any runtime resource is stored in the Blue Prism database and accessible via the Control Room. |
|
Hide the Digital Exchange tab |
If enabled, the Digital Exchange tab is hidden from the Blue Prism interactive client. |
|
Require secure inbound instructional communications. |
Only runtime resources which use the /sslcert switch will be able to successfully establish a connection with the platform. The /sslcert switch requires all inbound instructional connections to runtime resources to be subject to certificate-based encryption. This affects programmatically controlled robots such as those hosting web services. Disable this setting for troubleshooting purposes |
|
Allow anonymous public runtime resources |
When disabled, requires runtime resources to explicitly authenticate when connecting to the platform. This is not appropriate when the environment is configured to use Single Sign-on for user access if runtime resources are hosted outside of the common Active Directory Forest. Enable this setting for troubleshooting purposes |
|
Prevent registration of new runtime resources |
When enabled, no new runtime resources can be introduced to the platform. This should only be enabled once all required runtime resources have connected for the first time. Disable this setting for troubleshooting purposes |
|
Session Management enforces permissions of controlling user |
Enabled by default and recommended. If enabled, when session control actions are requested the permissions of the controlling user are validated. If disabled, the session control actions validate the permissions of the account used to authenticate the runtime resource against the environment. |
|
Resource registration and addressing |
Indicates whether FQDN names will be used to register runtimes within the database, and for subsequently establishing communications.
|
|
Enable Unicode support for session logs |
When enabled, Unicode characters are stored in session logs. This setting can only be changed while there are no pending or running sessions. |
|
Save environment data for clients, runtime resources and servers to the database |
Enabled by default. If enabled, environment data for clients, runtime resources and servers are written to the database when a device comes online. |
|
Tesseract engine |
Allows users to select the appropriate Tesseract engine version: 0 - Legacy engine only - Operates Tesseract V4.0.0 in compatibility mode that mimics the behavior of V3.05.01 – ideal if troubleshooting following an upgrade. 1 - Neural nets LSTM engine only - Operates with the new OCR engine, that uses a neural network system based on Long Short-Term Memory (LSTM). 2 - Legacy plus LSTM engine - Operates in compatibility mode with added support for LSTMs. 3 - Default, based on what is available - Uses the best available engine for the version of Tesseract that is currently in use in the installed version of Blue Prism. |
|
Environment Themes |
Enables users to apply a theme to easily differentiate between environments. A basic theme can be configured for an environment by selecting a name for the environment and background and foreground colors for title labels and status bars. The colors selected will display in the Preview box. The changes will be applied to the Blue Prism client window immediately, however any open Studio windows will have to be closed and reopened and other logged in users will have to sign out and sign back into the environment to reflect the changes. |
|
Enable Offline Help |
Blue Prism uses a help system that requires access to the internet. Where internet access is not available, the help files can be requested from Blue Prism and hosted internally or on local machines. Select this option to enable offline help and specify the location in the Base URL field. |
| Use fixed browser extension port (31924) only |
The Chrome and Firefox browser extensions use ephemeral ports to communicate with Blue Prism. Select this option if you require to continue using a fixed port for communication between Blue Prism and the Chrome and Firefox browser extensions. Runtime resources must be restarted for any change to this setting to take effect. |
We recommend that the installation is manually verified by carrying out some simple tasks within the system and confirming that they execute successfully.
For step-by-step instructions, see to Verify an Installation.
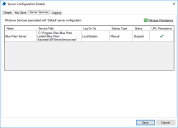
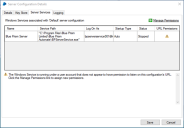
Blue Prism application server services are configured using BPServer.exe. This application is provided as part of the Blue Prism installation and is used to define and configure the services that are available on a given server.
The Blue Prism server configuration utility will be used to configure server profiles which contain the settings that the service will use. Additionally it can be used to create additional Windows Services for situations where the default profile is renamed, or additional profiles are added.
The configuration includes:
- Selecting the mode that inbound connections will be require to used
- Defining the hostname or IP address binding and port that the service will listen on
- Specifying database connection information.
- Configuring an encryption scheme that will be used for data encryption in that environment.
- Where appropriate, selecting which certificate will be used to secure inbound connections.
- Validating that there is an appropriate Windows Service configured, and that the service logon user has been added to the appropriate access control list (ACL).
- Navigate to the Blue Prism installation directory, typically C:\Program Files\Blue Prism Limited\Blue Prism Automate and launch BPServer.exe.
-
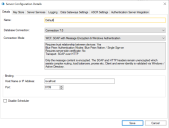
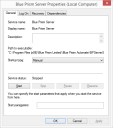
Click New configuration to create a server configuration.
- Add the required details. Ensure that the connection mode, bindings and listening port are correct.
- Name – Name for the server profile. The first one must be called Default.
- Database Connection – Connection used to connect to the database.
- Connection Mode – Connection mode to be used by connecting devices.
- Binding – Optional binding for the endpoint for scenarios where requests must be received on a specific URL or address.
- Port – Server listening port.
Disable Scheduler – Indicates whether this server should have the scheduler enabled.
-
If a connection mode has been selected which requires a certificate to be configured, a message will be displayed and the Certificates tab will become available. This allows a certificate that has been configured as a Computer certificate on the local device to be associated with the server service.
If the certificates tab is not displayed, progress to the next step.
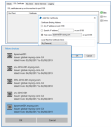
- Select to add a new certificate binding and enter the binding information and which store on the local device the certificate has been installed in.
- Click OK to launch the Windows certificate selection utility and pick the appropriate certificate.
- It is necessary to select a certificate that matches the binding on the details tab.
- Select to add a new certificate binding and enter the binding information and which store on the local device the certificate has been installed in.
-
Select the Key Store tab and click New.
An entry must be made for each Encryption Scheme defined via the Blue Prism client that is configured to use a key stored on the application server.
The name of the Encryption Schemes must be an exact match of those configured in the client.
When using a default configuration only one Encryption Scheme will be required named Default Encryption Scheme.
- If this is the first application server that is being configured for the environment, select AES-256 as the encryption method.
-
Click Generate Key followed by OK.
If this is an additional application server instance for an existing Blue Prism deployment, the algorithm and key must match that on the pre-existing server.
Commonly security conscious users will also select to store keys separately in individual files so that the target locations can controlled.
A copy of each key must be backed up in a secure location – it will be needed to retrieve encrypted data if the server fails.
-
Review the settings on the Server Services tab to ensure that no problems have been identified so far.
- Click Save.
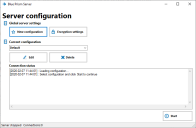
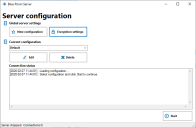
The encryption settings of the BP server can be configured to protect the server's encryption keys when they are stored in the application server.
Certificate encryption of server configuration files is recommended for deployments that need to be the most secure and it requires a locally-deployed certificate with an associated private key to be available. See Using certificate encryption for details.
- Navigate to the Blue Prism installation directory, by default C:\Program Files\Blue Prism Limited\Blue Prism Automate and launch BPServer.exe.
-
Click Encryption settings to configure the encryption settings that will be applied to the information stored in the local configuration files used by the Blue Prism application server.
-
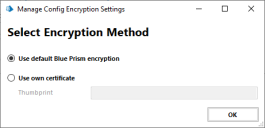
In the Select Encryption Method dialog, select to use either the default Blue Prism encryption or your own certificate. We recommend using your own certificate.
We recommend using your own certificate. See Using certificate encryption.
When selecting to use your own certificate, enter the thumbprint from your certificate, which is the automatically generated ID for the certificate.
- Click OK.
Using certificate encryption
If you have chosen to use certificate encryption for the application server configuration data, the following elements must be considered to ensure access for all relevant components and for continued successful encryption.
Certificate storage
The certificate used to encrypt server configuration data must use RSA encryption and contain a public/private key pair. The certificate must also be stored on the local machine in the following location:
[Certificates - Local Computer\Personal\Certificates].
Certificate access
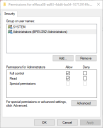
To ensure that the user configuring the Blue Prism server and the user account on which the server service runs have read access to the private keys on the certificate:
- In the Manage Computer Certificates window select the certificate to which you need to give read access.
- From the shortcut menu select All Tasks > Manage Private Keys.
-
In the Permissions dialog ensure the user account on which the server service is running has read access to the certificate. Add any users or groups that also need read access to the certificate.
If you have chosen to store encryption scheme keys in separate files, the certificate encryption will be applied to the separate files. If the location of the separate files is shared with other application servers, they will all need the same certificate to be stored locally and have a minimum of read access to the private key.
Encrypting server configuration data
When you use certificate encryption, all encrypted data from the server configuration is decrypted and held in protected memory. When a new encryption method or certificate thumbprint is selected, the file is saved, encrypting the secret data as they are read from protected memory and written to the file.
When you select certificate encryption, the following application server configuration data is encrypted:
- The encryption scheme key that is used to encrypt and decrypt sensitive information from the database for the Blue Prism server connection.
- The password used to connect to the database if using SQL Authentication for database connections.
Expired and missing certificates
The expiry date for custom encryption certificates for Blue Prism application server configuration files can be found in the Environment Summary report, they are also written to Blue Prism event logs. In addition, when logging into Blue Prism, users are notified if a certificate used to encrypt the Blue Prism application server configuration files is due to expire within the next seven days.
If a certificate expires it will stop working with the Blue Prism application server. Certificate encryption may also stop working in the following circumstances:
- The user account running the server doesn’t have access to the public and/or private key. In this instance, a message displays asking the user to reset the configuration.
- The certificate used for encryption is now missing from the certificate store.
- The user account no longer has access to the local computer certificate store. In this instance, an error will display at start up when trying to load the certificate.
If the certificate used for encryption cannot be accessed or restored the user configuring the Blue Prism server will need to recreate the server configuration profiles. To do this, delete the Automate.config file, which is located in: ProgramData\Blue Prism Limited\Automate V3. A new Automate.config file will be automatically created when the BPServer.exe is launched. An encryption scheme and new certificate can then be applied to the new server configuration file.
The default installation of Blue Prism creates a Blue Prism Server service which is configured to use the server settings profile named Default. If a profile of a different name has been used, the server configuration utility can be used to create a Windows service associated with the custom profile.
The Windows service should be configured from the Windows Services management console on the local device. The main settings to be configured are:
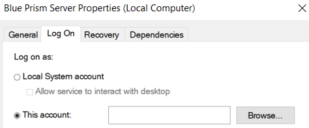
- Startup type – By default this is set to Manual however it is recommended that for most environments it should be set to Automatic.
- Log On – The default account used by Blue Prism is Local System however this can be configured to be custom account.
Where Windows Authentication is used for the Blue Prism Server profile to communicate with the database, it is the account specified here that will be used by the service when connecting to the database.
When SQL is secured using Windows Authentication, the configured Windows Service account will need to have appropriate (minimum) access to the SQL database.
When Blue Prism is configured to use Single Sign-On, the configured Windows Service account will need to have appropriate permissions to access the directory services provider and query users and group membership. The specific permissions that are required in relation to Active Directory will be dependent on environmental factors and therefore assistance from the Active Directory administrator team within the target environment is likely to be required.
When starting the service, if it won’t start or if it stops immediately, it can indicate a configuration problem. Check the Blue Prism Application Log within Windows Event Viewer for additional information about the problem.
Use the Blue Prism Server configuration utility to re-validate the service configuration.
Common configurations such as where Blue Prism is configured to use Windows Authentication to authenticate against SQL may result in an error. This can occur if a non-admin user has been configured as the service log on account. In such situations, alerts similar to the below may be presented:
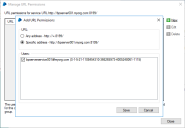
The Manage Permissions functionality can be used to grant the service account the appropriate permissions to listen on the defined port. The following rules must be considered:
- If the service is configured to use a binding, a specific address permission must be created.
- If the service is not configured to use a binding, a non-specific address permission must be used.
It is not possible to use an address containing a strong wildcard if the service will be using a defined binding.
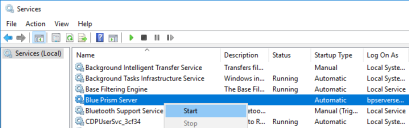
Use the Windows Services management console to start the service.
If the service will not start, or starts and then immediately stops there is a problem with the configuration of the service. For more information, review Troubleshooting an installation.
The server service can be tested locally be configuring an additional Blue Prism connection on the local device that is configured to connect via the newly configured server service.
-
Launch Blue Prism and click Configure connection.

- This will launch the wizard that can be used to provide the connection information:
- Connection name – Friendly name for the connection
- Connection type – The type of connection to use
- Blue Prism server – Address of the server. Must match the server binding, and be resolvable.
- Connection mode – Connection mode to use. Must match the setting on the Server
- Server port – The port that the server is listening on.
Ordered sessions – This is enabled by default and controls whether WCF connection sessions must be transmitted in order or not. Disabling this setting will reduce the amount of time a Blue Prism interactive client takes to connect to a large number of runtime resources.
-
Click Test Connection to verify that a connection can be established.
If the connection cannot be verified, this indicates that there is a problem with establishing a connection with the application server. For more information, review Troubleshooting an installation.
Administrators can now use the two connections configured in the local Blue Prism client to validate:
- Direct connections to the Blue Prism database.
- Connections to the environment via the application server.
If using the following connection modes with a Blue Prism Server connection, a Service Principal Name (SPN) must be configured against the Active Directory (AD) account under which each Blue Prism Server service instance is running:
- WCF: SOAP with Message Encryption & Windows Authentication
- WCF: SOAP with Transport Encryption & Windows Authentication
- .NET Remoting Secure
This is because when a Blue Prism interactive client or a runtime resource connects to an application server using one of the connection modes above, the Microsoft Negotiate Security Package is used to select the best Security Support Provider (SSP) to authenticate the connection. The internal code of the Blue Prism interactive client provides the expected SPN to the Microsoft Negotiation Security Package, which prompts Microsoft Negotiation to select the Kerberos SSP over New Technology LAN Manager (NTLM) SSP, provided the SPN is present in Active Directory.
If the SPN is not present in Active Directory, Kerberos authentication will fail. See this Knowledge Base article for more details on the Windows security update for CVE-2022-21920 which affects this behavior.
From Blue Prism 6.9.1, if the SPN is not present in Active Directory, and if the /forcentlm <flag> is set in Automate C, the NTLM SSP will be used.
It is recommended to contact your organization's IT team for assistance with this configuration, and that you first test the configuration in a non-production environment.
This configuration applies to all Blue Prism environments, however, if the Active Directory account under which your BP Server instances are running resides in a different domain to the Active Directory account used for the Blue Prism interactive client and runtime resource, we recommend you do not install the Windows security update for CVE-2022-21920. If you have already installed it, we recommend that you uninstall it.
From Blue Prism 6.9.1, the additional configuration outlined below is required if the Active Directory account under which your BP Server instances are running resides in a different domain to the Active Directory account used for the Blue Prism interactive client and runtime resource.
To configure the SPN, follow the steps below on each Blue Prism Server Service instance:
-
Log into the Blue Prism Server using a Privileged Windows User Account that is a member of the Domain Admins or Enterprise Admins group.
See the Microsoft documentation in this topic for further details including required permissions. This is an essential step to review with your organization's IT team to ensure that the Setspn command does not fail to execute due to missing account permissions.
-
Open Command Prompt as an administrator on the application server and run the command below.
If the Blue Prism Server is running as a Local System account:
CopySetspn -S -C HTTP/SERVER_FQDN:SERVER_PORT/BPServer COMPUTER_HOSTNAMEIf the Blue Prism Server is running as a user account:
CopySetspn -S -U HTTP/SERVER_FQDN:SERVER_PORT/BPServer DOMAIN\UsernameWhere:
-
HTTP accounts for both HTTP and HTTPS. Do not change the command to include HTTPS specifically as the configuration will fail.
- SERVER_FQDN:SERVER_PORT must be the Fully Qualified Domain Name (FQDN) of the Blue Prism application server.
-
COMPUTER_HOSTNAME is the hostname of the computer if BP Server Service is running as a Local System account.
-
DOMAIN\Username is the domain username if BP Server Service is running as a user account.
This should match the Log on as setting in the Blue Prism Server Properties (Local Computer) window.
Example with local system:
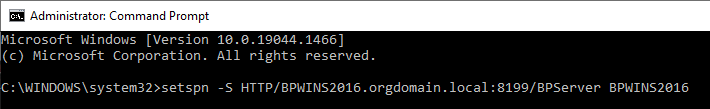
Example with DOMAIN\Username:
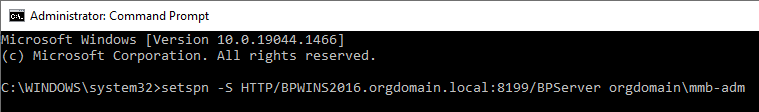
-
-
After setting the SPN you will need to wait for the Kerberos ticket cache to renew (the default setting is 15 minutes, but it can be changed via Group policy). For more details, see the Kerberos authentication documentation.
Alternatively, you can either:
- Restart the Blue Prism interactive client or runtime resource; or
-
On the machine running the interactive client or runtime resource, open Command Prompt and run Klist purge to refresh the Kerberos tickets.
This command should not be performed within an elevated Command Prompt as it will not purge all the user Kerberos tickets.
- Check that this is working as expected by connecting to the Blue Prism Server from a Blue Prism interactive client running on another machine.
-
Repeat the steps above on each instance of the Blue Prism Server Service running on every Blue Prism Server.
Check SPN entries and remove an incorrect SPN
-
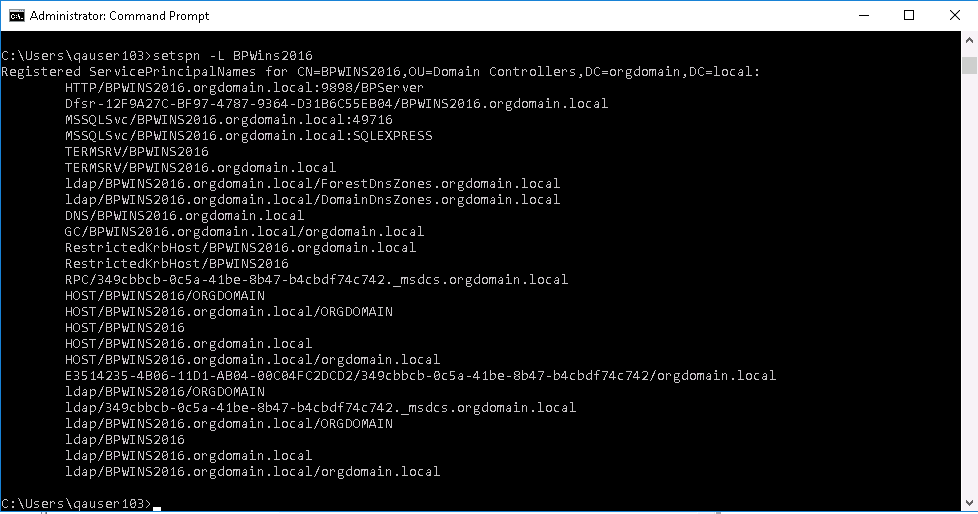
To check SPN entries for troubleshooting purposes, you can see a list of the added SPNs on the application server using the following command:
-
Check the entries for the SPNs you added for the BP Server Service. You can remove the one added in error using the command listed below:
CopySetspn -D SPN_NAME ACCOUNTNAMEWhere SPN_NAME is the name displayed in the SPN entries list, for example, HTTP/SERVER_FQDN:SERVER_PORT/BPServer.
Example of SPN list:
Additional configuration for Blue Prism application servers in load balanced environments
It is essential that all instances of the Blue Prism Server Service in the same load balancer pool are running under the same service account and the SPN is registered to this account.
Additionally, it is recommended to register SPNs for the application server's FQDNs to the same service account, as this will allow for testing of a direct connection to the application servers. For more details, see SPN troubleshooting.
Additional configuration for Active Directory authentication in multi-forest environments
This functionality is only available from Blue Prism 6.9.1 onwards.
To support Kerberos authentication in Blue Prism environments configured to use Active Directory authentication in multiple forests, the following settings must be configured in Automate C:
- /setkerberosrealm – For example, /setkerberosrealm mycompany.com.This must be configured for each BP Server connection in the interactive client where the user's Kerberos realm is different to that of the account configured to run BP Server. The Kerberos realm is usually the same as the domain name, however, please check with your IT team for the correct value.
-
/forcentlm <flag> – For example, /forcentlm true. This forces Microsoft Negotiate Security Package to select New Technology LAN Manager (NTLM) as the Security Support Provider (SSP) when authenticating connections. This option is provided so that NTLM can be used when Kerberos is unavailable or not configured (see SPN configuration).
Please consult with your security team before enabling this option as NTLM is considered a less secure protocol.
 Docs
Docs