Service Principal Name (SNP) configuration for Kerberos authentication
If using the following connection modes with a Blue Prism Server connection, a Service Principal Name (SPN) must be configured against the Active Directory (AD) account under which each Blue Prism Server service instance is running:
- WCF: SOAP with Message Encryption & Windows Authentication
- WCF: SOAP with Transport Encryption & Windows Authentication
- .NET Remoting Secure
This is because when a Blue Prism interactive client or a runtime resource connects to an application server using one of the connection modes above, the Microsoft Negotiate Security Package is used to select the best Security Support Provider (SSP) to authenticate the connection. The internal code of the Blue Prism interactive client provides the expected SPN to the Microsoft Negotiation Security Package, which prompts Microsoft Negotiation to select the Kerberos SSP over New Technology LAN Manager (NTLM) SSP, provided the SPN is present in Active Directory.
If the SPN is not present in Active Directory, Kerberos authentication will fail. See this Knowledge Base article for more details on the Windows security update for CVE-2022-21920 which affects this behavior.
From Blue Prism 6.9.1, if the SPN is not present in Active Directory, and if the /forcentlm <flag> is set in Automate C, the NTLM SSP will be used.
It is recommended to contact your organization's IT team for assistance with this configuration, and that you first test the configuration in a non-production environment.
This configuration applies to all Blue Prism environments, however, if the Active Directory account under which your BP Server instances are running resides in a different domain to the Active Directory account used for the Blue Prism interactive client and runtime resource, we recommend you do not install the Windows security update for CVE-2022-21920. If you have already installed it, we recommend that you uninstall it.
From Blue Prism 6.9.1, the additional configuration outlined below is required if the Active Directory account under which your BP Server instances are running resides in a different domain to the Active Directory account used for the Blue Prism interactive client and runtime resource.
To configure the SPN, follow the steps below on each Blue Prism Server Service instance:
-
Log into the Blue Prism Server using a Privileged Windows User Account that is a member of the Domain Admins or Enterprise Admins group.
See the Microsoft documentation in this topic for further details including required permissions. This is an essential step to review with your organization's IT team to ensure that the Setspn command does not fail to execute due to missing account permissions.
-
Open Command Prompt as an administrator on the application server and run the command below.
If the Blue Prism Server is running as a Local System account:
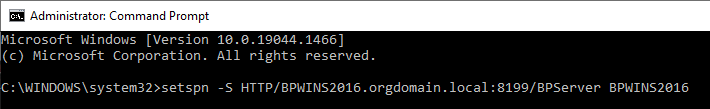
CopySetspn -S -C HTTP/SERVER_FQDN:SERVER_PORT/BPServer COMPUTER_HOSTNAMEIf the Blue Prism Server is running as a user account:
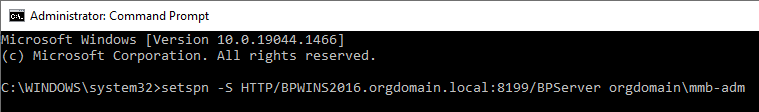
CopySetspn -S -U HTTP/SERVER_FQDN:SERVER_PORT/BPServer DOMAIN\UsernameWhere:
-
HTTP accounts for both HTTP and HTTPS. Do not change the command to include HTTPS specifically as the configuration will fail.
- SERVER_FQDN:SERVER_PORT must be the Fully Qualified Domain Name (FQDN) of the Blue Prism application server.
-
COMPUTER_HOSTNAME is the hostname of the computer if BP Server Service is running as a Local System account.
-
DOMAIN\Username is the domain username if BP Server Service is running as a user account.
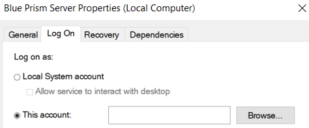
This should match the Log on as setting in the Blue Prism Server Properties (Local Computer) window.
Example with local system:
Example with DOMAIN\Username:
-
-
After setting the SPN you will need to wait for the Kerberos ticket cache to renew (the default setting is 15 minutes, but it can be changed via Group policy). For more details, see the Kerberos authentication documentation.
Alternatively, you can either:
- Restart the Blue Prism interactive client or runtime resource; or
-
On the machine running the interactive client or runtime resource, open Command Prompt and run Klist purge to refresh the Kerberos tickets.
This command should not be performed within an elevated Command Prompt as it will not purge all the user Kerberos tickets.
- Check that this is working as expected by connecting to the Blue Prism Server from a Blue Prism interactive client running on another machine.
-
Repeat the steps above on each instance of the Blue Prism Server Service running on every Blue Prism Server.
Check SPN entries and remove an incorrect SPN
-
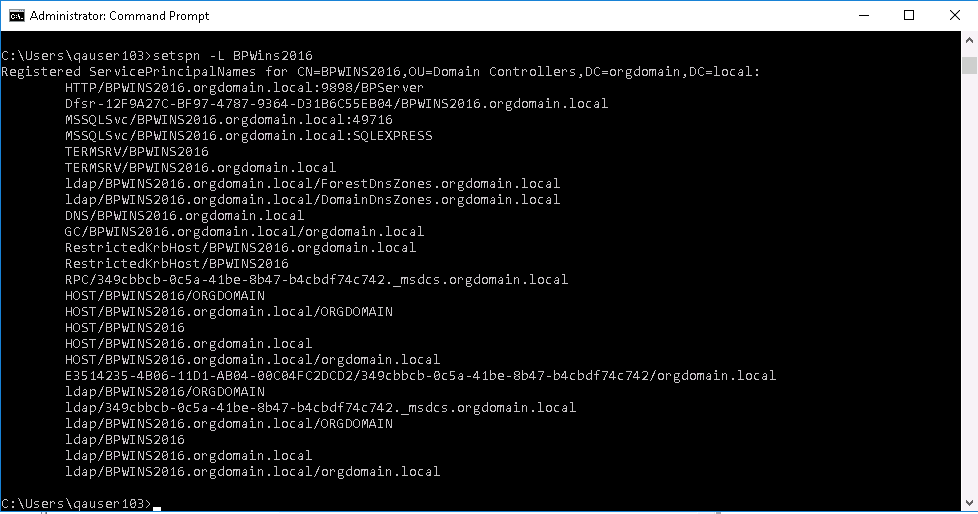
To check SPN entries for troubleshooting purposes, you can see a list of the added SPNs on the application server using the following command:
-
Check the entries for the SPNs you added for the BP Server Service. You can remove the one added in error using the command listed below:
CopySetspn -D SPN_NAME ACCOUNTNAMEWhere SPN_NAME is the name displayed in the SPN entries list, for example, HTTP/SERVER_FQDN:SERVER_PORT/BPServer.
Example of SPN list:
Additional configuration for Blue Prism application servers in load balanced environments
It is essential that all instances of the Blue Prism Server Service in the same load balancer pool are running under the same service account and the SPN is registered to this account.
Additionally, it is recommended to register SPNs for the application server's FQDNs to the same service account, as this will allow for testing of a direct connection to the application servers. For more details, see SPN troubleshooting.
Additional configuration for Active Directory authentication in multi-forest environments
This functionality is only available from Blue Prism 6.9.1 onwards.
To support Kerberos authentication in Blue Prism environments configured to use Active Directory authentication in multiple forests, the following settings must be configured in Automate C:
- /setkerberosrealm – For example, /setkerberosrealm mycompany.com.This must be configured for each BP Server connection in the interactive client where the user's Kerberos realm is different to that of the account configured to run BP Server. The Kerberos realm is usually the same as the domain name, however, please check with your IT team for the correct value.
-
/forcentlm <flag> – For example, /forcentlm true. This forces Microsoft Negotiate Security Package to select New Technology LAN Manager (NTLM) as the Security Support Provider (SSP) when authenticating connections. This option is provided so that NTLM can be used when Kerberos is unavailable or not configured (see SPN configuration).
Please consult with your security team before enabling this option as NTLM is considered a less secure protocol.
 Docs
Docs