Active Directory configuration
Blue Prism supports single sign-on using Microsoft Active Directory Domain Services which allows users who have been authenticated by the operating system, and who are members of appropriate domains and forests, to log into Blue Prism without resubmitting their credentials.
Blue Prism provides two types of environments for managing Active Directory authentication to the platform:
- Multi-authentication environment – supports Active Directory accounts where roles are mapped to individual users in Blue Prism. In multi-authentication environments, Active Directory users can be contained in multiple domains and multiple forests.
- Single-authentication environment – referred to as Active Directory Single Sign-On authentication in previous versions of Blue Prism, it supports Active Directory accounts where roles are mapped to Active Directory security groups. In single-authentication environments, Active Directory users can be contained within multiple domains but only a single forest.
When configuring Blue Prism to use Active Directory authentication, the database must be configured at the time of creation to use either a multi-authentication or a single-authentication environment. For further details, see Create a new database.
Active Directory configuration in a single-authentication environment
Where Blue Prism is deployed within a single Active Directory forest, it can be configured to allow users to authenticate against the platform using single sign-on. It essentially requires an Active Directory security group to be mapped to each relevant Blue Prism security role after which users will be granted access to the platform based on their Active Directory security group membership.
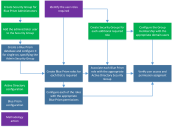
The steps required to configure Blue Prism integration with Active Directory for single sign-on in a single-authentication environment are illustrated in the diagram below:
After the database has been created with the appropriate settings to indicate that Active Directory authentication in a single-authentication environment should be used for the Blue Prism platform, the users and roles must be configured in the Blue Prism product.
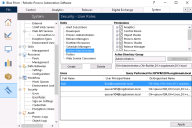
- Click System and select Security - User Roles from the navigation tree.
-
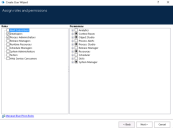
For each role, configure the permissions that should be granted and select the Active Directory security group whose members should be assigned to this role.
Blue Prism roles must be associated with security groups created in Active Directory. Single sign-on for Blue Prism does not support built-in groups or those with derived membership such as domain users or authenticated users. It is also recommended that the security groups used do not contain Foreign Security Principals.
- Once complete, click Apply.
Users who belong to the groups that have been configured should now be able to log into Blue Prism and perform the actions permitted by the corresponding Blue Prism role (as indicated by the tree on the right).
Users may have to log out of Windows and log back in again for Active Directory changes to take effect.
Active Directory configuration in a multi-authentication environment
Blue Prism can also be configured to allow users to authenticate against the platform using single sign-on when it is deployed within multiple Active Directory forests. In this scenario, users created in the Active Directory domains and forests are then mapped to Blue Prism roles via the Create new user wizard in Blue Prism. Multiple roles can be selected and then assigned to one or more Active Directory users.
Blue Prism administrators who are members of an Active Directory domain must enable Active Directory authentication on the System > Security - Sign-on Settings screen in Blue Prism before creating Active Directory users in a multi-authentication environment.
For more details, see Single sign-on.
 Docs
Docs