Install and configure the web server – Interact
Install and configure the Web Server as per the installation instructions in the Blue Prism Hub installation guide.
Do not log into Blue Prism Hub and configure the environment. This must be done after you have installed Blue Prism Interact.
Instructional videos on how to install the prerequisite software and Blue Prism Interact are available from: https://bpdocs.blueprism.com/en-us/video/installation.htm.
Install Prerequisites
The system requires IIS Web Server and the .NET Core components to be installed. These are all installed as part of a successful installation of Blue Prism Hub. Interact can coexist alongside the Hub web services. See Prerequisites for details.
Configure SSL Certificates
During the installation process you will be asked for the SSL certificates for the websites that are being set up. Depending on your infrastructure and IT organization security requirements, this could be an internally created SSL certificate or a purchased certificate to protect the websites.
When generating a certificate, enter the host name in lowercase characters. If you do not use all lowercase, you may experience a naming mismatch between the name in the certificate and the host name when using the Hub installer. This could result in the certificate failing to be applied and the installer preventing you from progressing with the installation.
The installer can be run without the certificates being present, though for the sites to operate, the bindings in the IIS websites will need to have valid SSL certificates present.
The table below details the required Interact SSL certificates.
|
Website in IIS |
Default URL |
|---|---|
|
Websites with a UI for use by end-users |
|
|
Blue Prism – Interact |
https://interact.local |
|
Websites for use by the application only (services) |
|
|
Blue Prism – IADA |
https://iada.local |
|
Blue Prism – Interact Remote API |
https://interactremoteapi.local |
The default URLs shown above are suitable for a standalone environment, such as a test environment. Your organization’s DNS and Domain structures must be considered when choosing host names for your installation.
Self-signed certificates
Self-signed certificates can be used but are only recommended for Proof of Concept (POC), Proof of Value (POV) and Development environments. For production environments, use certificates from your organization's approved certificate authority. It is recommended that you contact your IT Security team to check what their requirements are.
To generate and apply a self-signed certificate for SQL Server:
Microsoft provide a script that can be used to generate a self-signed certificate for SQL Server. For more information, see Microsoft's documentation. It is important that the fully qualified domain name (FQDN) used by the SQL Server matches the FQDN defined in the certificate. If these do not match, a connection to the database will not be established and your installation will not function correctly.
-
Run PowerShell as an administrator and execute the Microsoft script with the information for your SQL Server.
This generates the certificate and installs it on the SQL Server.
-
On your SQL Server:
-
Enable access to the certificate's private key for the SQL Server service account. To do this:
-
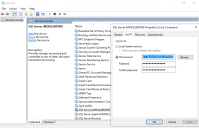
If you do not already know it, find your service account name for your SQL Server. This is shown on the Log On tab of the SQL Server Properties, which can be accessed from Services on your SQL Server.
-
On your SQL Server, open Certificate Manager.
-
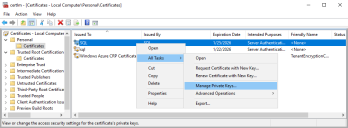
Expand Personal, then expand Certificates, right-click SQL, and then select All Tasks and click Manage Private Keys...
-
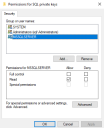
In the Permissions for SQL private keys dialog, add your SQL Server service account with Read permissions. For example:
-
Click OK to apply the changes and close the dialog.
-
-
Enable SSL on your SQL Server and specify the certificate. To do this:
-
From the Windows task bar, open SQL Server Configuration Manager.
-
In the SQL Server Configuration Manager, expand SQL Server Network Configuration and right-click Protocols for <SqlServerInstanceName>, and then click Properties.
-
In the Protocols for <SqlServerInstanceName> Properties dialog, select the Certificate tab, and then select or import the required certificate.
-
Click Apply.
-
Click OK to close the Properties dialog.
-
-
Restart the SQL Server service.
-
Copy the certificate C:\sqlservercert.cer. You will need to add this to the Hub and Interact website host servers.
-
-
On the website host servers:
-
Paste the sqlservercert.cer into the website host servers for Hub and Interact.
-
Add the certificate to the server's Trusted Root Certification Authorities certificate store. To do this:
-
Double-click on the certificate and click Install Certificate....
The Certificate Import Wizard displays.
-
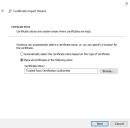
On the Welcome page, select Local Machine under Store Location and click Next.
-
On the Certificate Store page, select Place all certificates in the following store and enter Trusted Root Certification Authorities.
-
Click Next and follow the wizard through to completion.
-
-
Test the connection from the website host server to the SQL Server.
-
To generate a self-signed certificate for a website:
-
Run PowerShell as an administrator and use the following command, replacing [Website] and [ExpiryYears] with appropriate values:
CopyNew-SelfSignedCertificate -CertStoreLocation Cert:\LocalMachine\My -DnsName "[Website].local" -FriendlyName "MySiteCert[Website]" -NotAfter (Get-Date).AddYears([ExpiryYears])For example:
CopyNew-SelfSignedCertificate -CertStoreLocation Cert:\LocalMachine\My -DnsName "authentication.local" -FriendlyName "MySiteCertAuthentication" -NotAfter (Get-Date).AddYears(10)This example creates a self-signed certificate called MySiteCertAuthentication in the Personal Certificates store, with the Subject authentication.local and is valid for 10 years from the point of creation.
When generating a certificate, enter the host name ([Website]) in lowercase characters. If you do not use all lowercase, you may experience a naming mismatch between the name in the certificate and the host name when using the Hub installer. This could result in the certificate failing to be applied and the installer preventing you from progressing with the installation.
- Open the Manage Computer Certificates application on your web server (type manage computer into the search bar).
-
Copy and paste the certificate from Personal > Certificates to Trusted Root Certification > Certificates.
- Repeat this process for each website.
This process is not recommended for production environments.
Run the following PowerShell commands:
New-SelfSignedCertificate -CertStoreLocation Cert:\LocalMachine\My -DnsName "interact.local" -FriendlyName "MySiteCertInteract" -NotAfter (Get-Date).AddYears(10)
New-SelfSignedCertificate -CertStoreLocation Cert:\LocalMachine\My -DnsName "iada.local" -FriendlyName "MySiteCertIADA" -NotAfter (Get-Date).AddYears(10)
New-SelfSignedCertificate -CertStoreLocation Cert:\LocalMachine\My -DnsName "interactremoteapi.local" -FriendlyName "MySiteCertIRA" -NotAfter (Get-Date).AddYears(10)Once created, open the Local Machine certificate manager (certlm) and copy and paste the certificates into the trusted root certificate store.
Create an offline certificate request
To create an offline certificate request, for each certificate follow this procedure:
- Open the Manage Computer Certificates application on your web server (type managed computer into the search bar).
-
Right-click Personal > Certificates and select All Tasks > Advanced Operations > Create Custom Request from the shortcut menu.
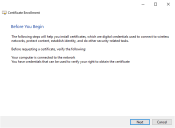
The Certificate Enrollment wizard displays.
-
Click Next.
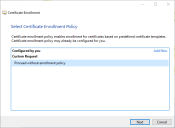
- Select Proceed without enrollment policy and click Next.
-
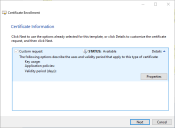
On the Custom request screen, click Next.
-
On the Certificate Information screen, click the Details drop-down and click Properties.
- On the General tab in the Certificate Properties dialog, enter a friendly name and description based on the website this certificate will be applied to.
-
On the Subject tab change the subject name type to Common name, enter the website URL in the Value field and click Add.
The CN (common name) will display in the right-hand panel.
- On the Extensions tab, click Extended Key Usage, select Server Authentication and click Add.
- On the Private Key tab, click Key options, select a key size of your choice and select Make private key exportable.
- Still on the Private Key tab, click Hash Algorithm and select a suitable Hash (optional).
-
Click OK.
You are returned to the Certificate Enrollment screen.
- Click Next.
- Add a file name and path and click Finish.
After creating your certificate request, you will need to submit it to a Certificate Authority so they can process your request and issue a certificate. The certificate request is a text file. Usually, you are required to copy the text from the file and enter it into an online submission form on the Certificate Authority website. You will need to contact your Certificate Authority directly for instructions on the process for submitting your certificate request.
 Docs
Docs