Active Directory authentication
Active Directory authentication can only be enabled on the Authentication Settings page if the server hosting Authentication Server is a member of an Active Directory domain.
To enable or disable Active Directory authentication:
- Use the slider to toggle to the required position:
- Cross indicates off
- Tick indicates on
- Click OK to accept the confirmation message.
You can only disable Active Directory authentication if there is at least one Hub administrator in the system who can sign in using one of the other authentication types. A check is carried out to identify whether there are any active administrator users configured to log in using any of the other enabled authentication types.
Once enabled, you can add Active Directory users on the Add user page and they can log into Hub directly using the Log in using Active Directory option.
This does not apply to LDAP users who will still be required to enter their credentials.
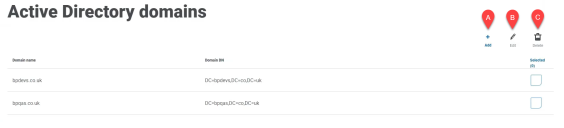
Active Directory domains
The Active Directory domains page allows you to view, add, edit, and delete Active Directory domains and associated credentials stored in the Authentication Server database.
To open the Active Directory domains page, click your profile icon to open the Settings page, click Authentication settings and then click View domains.
You only need to add new Active Directory domains for multi-forest environments with one-way trust relationships. For more details, see Active Directory authentication.
The Active Directory domains page provides you with the following information and functions:
- Add – Add a new Active Directory domain.
- Edit – Edit the details of an existing Active Directory domain. You can only edit one domain at a time.
- Delete – Delete one or more Active Directory domains.
Add a domain
-
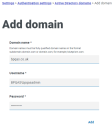
On the Active Directory domains page, click Add.
The Add domain page displays.
-
Enter a domain name.
This must be the fully qualified domain name (FQDN) using the format subdomain.domain.com or domain.com.
-
Enter the username and password for the domain. Usernames must be in the format [email protected] or DOMAIN\username. The credentials must be requested from a system administrator beforehand.
Active Directory domain credentials are stored in the database and are encrypted before storage. The credentials stored for each domain must be that of an Active Directory service account. The service account password must not expire, the service account must not be a user account, and should follow Active Directory service account best practices.
-
Click Add.
The domain name and credentials are validated against the Active Directory domain controller and the added domain displays in the domains list.
Edit a domain
-
On the Active Directory domains page, select a domain and click Edit.
You can only select one domain at the time.
-
Change the information as required. If you want to edit the domain name, you must delete this domain and create a new domain.
-
Click Save to apply your changes.
Delete domains
-
On the Active Directory domain, select the required domain(s) and click Delete.
A message displays asking you to confirm the deletion.
- Click Yes to delete the selected domain(s) or No to cancel.
Trust relationship between domains
For multi-forest environments, trust relationships must be configured between domains. These can be two-way or one-way to the domain that should be trusted.
For example:
- In a one-way trust between Domain A and Domain B, users in Domain A can access resources in Domain B. However, users in Domain B cannot access resources in Domain A.
- In a two-way trust, Domain A trusts Domain B and Domain B trusts Domain A. This means that authentication requests can be passed between the two domains in both directions.
Two-way trusts do not require the user to provide domain credentials if the Authentication Server application pool user has relevant read access to the domain that the user belongs to. In these examples, the web server hosting Authentication Server would reside in Domain B. Two-way trusts require credentials to be provided when the user need to query a trusted domain using an account different to the Authentication Server application pool user. One-way trusts require a domain with credentials to be created.
The following trust types are supported:
- External
- Parent-child
- Tree-root
- Forest
Active Directory user management
|
If Active Directory authentication has been enabled on the Authentication settings page, you must select how to manage access for Active Directory users in Hub by enabling at least one of the following options on the Authentication settings page:
For details on how to assign Active Directory users and security groups to roles, see Roles and permissions. Watch this video for an overview of Active Directory integration with Authentication Server. |
This video demonstrates the configuration of Authentication Server using Hub 4.6 and Blue Prism 7.1. If you are using later versions, there may be some differences. For more information, see the Authentication Server configuration documentation. |
 Docs
Docs