Active Directory domains
Blue Prism administrators are able to view, add, edit, and delete Active Directory domains and associated credentials stored in the Blue Prism database.
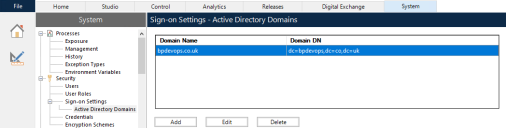
To access and manage Active Directory domains in Blue Prism, navigate to System > Security > Sign-on Settings > Active Directory Domains.
You only need to add new Active Directory domains in multi-forest environments with a one-way trust relationship. For more details, see Trust relationships between domains.
Prerequisites
The following prerequisites must be met before adding Active Directory domains:
- Ensure the encryption scheme is configured – Active Directory domain credentials are encrypted in the Blue Prim database using the default encryption scheme, so an encryption scheme must be configured before adding domains. It is recommended to store the encryption key on the application server. For more details, see Encryption schemes.
-
Ensure the encryption key is accessible to the Blue Prism API – If the encryption key is stored on the application server, additional steps must be taken to make the encryption keys available to the Blue Prism API. This is to ensure that Active Directory users across multiple domains are able to use the browser-based Control Room. To allow this, the Blue Prism API must be able to decrypt the domain credentials using the encryption scheme stored on the application server. For more details, see API configuration.
Add a domain
-
On the Sign-on Settings - Active Directory Domains screen, click Add.
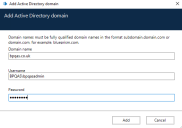
The Add Active Directory domain screen displays.
-
Enter a domain name.
This must be the fully qualified domain name (FQDN) using the format subdomain.domain.com or domain.com.
-
Enter the username and password for the domain. Usernames must be in the format [email protected] or DOMAIN\username. The credentials must be requested from a system administrator beforehand.
Active Directory domain credentials are stored in the database and are encrypted before storage. The credentials stored for each domain must be that of an Active Directory service account. The service account password must not expire, the service account must not be a user account, and should follow Active Directory service account best practices.You only need to enter domain credentials in a multi-forest environment with a one-way trust.
-
Click Add.
The domain name and credentials are validated against the Active Directory domain controller and the added domain displays in the domains list.
Edit a domain
-
On the Sign-on Settings - Active Directory Domains screen, select a domain and click Edit.
You can only edit one domain at a time.
-
Change the information as required. You will have to re-enter your password.
You cannot edit domain names.
-
Click Save to apply your changes.
Delete domains
-
On the Sign-on Settings - Active Directory Domains screen, select the required domain(s) and click Delete.
A message displays asking you to confirm the deletion.
- Click Delete to delete the selected domain(s).
Trust relationships between domains
For multi-forest environments, trust relationships must be configured between domains. These can be two-way or one-way to the domain that should be trusted.
For example:
- In a one-way trust between Domain A and Domain B, users in Domain A can access resources in Domain B. However, users in Domain B cannot access resources in Domain A.
-
In a two-way trust, Domain A trusts Domain B and Domain B trusts Domain A. This means that authentication requests can be passed between the two domains in both directions.
Two-way trusts do not require the user to provide domain credentials if the user running the Blue Prism application server has relevant read access to the domain that the user belongs to. In these examples, the Blue Prism application server would reside in Domain B. Two-way trusts require credentials to be provided when the user needs to query a trusted domain using an account different to the account running the Blue Prism application server. One-way trusts require a domain with credentials to be created.
The following trust types are supported:
-
External
-
Parent-child
-
Tree-root
-
Forest
For more information, see Supported Active Directory infrastructure.
 Docs
Docs