Audit logs
Blue Prism provides rigorous auditing features which record the actions of users. All important changes performed by a user are recorded in a log file for later inspection.
Examples of actions recorded include:
- Logging into Blue Prism
- Running a process
- Deleting a process
- Changing user permissions
- Changing a user's name, or any other part of a user's configuration
Individual revisions to processes are also recorded, and these changes may be tracked over time using the process history tool.
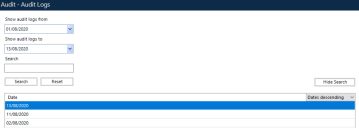
Access and search the audit logs
You can access the audit logs via System Manager, under Audit - Audit Logs. A search by date function returns the last seven days of logs. You can also filter the logs recorded for a particular date by a specific search term, and sort the logs by ascending or descending dates.
To view the log data for a set of dates, select the dates of interest from the calendar and click Search. Double-click the audit log in the results list to open the Audit Log Viewer.
Audit log viewer
The audit log viewer displays the logs in a table with several columns which record the date and time of each event, the user involved, the action, and any additional comments.
Avoid naming confusion
Where a user or process is involved in an audit record (ie a row in the table), the current name of the user will be displayed and not the name of the user as it was at the time. For example, if the user "John Smith" deleted a process and subsequently had his username changed to "James Brown", the name "James Brown" would appear in the table, rather than the name of the user as it was at the time the action took place (ie "John Smith").
Note that further confusion may arise if a new user was since added to the system who coincidentally had the name "John Smith", matching the former name of the existing user "James Brown".
While seemingly confusing, this feature simplifies the log data greatly, since any name read from the log immediately identifies the user/process/resource pc in question; it eliminates the need to track back through the log and work out which user had which name at which time. This advantage is especially great on a system with a large number of users/processes, and which has a history stretching back for many years.
 Docs
Docs