Securing Blue Prism Network Connectivity
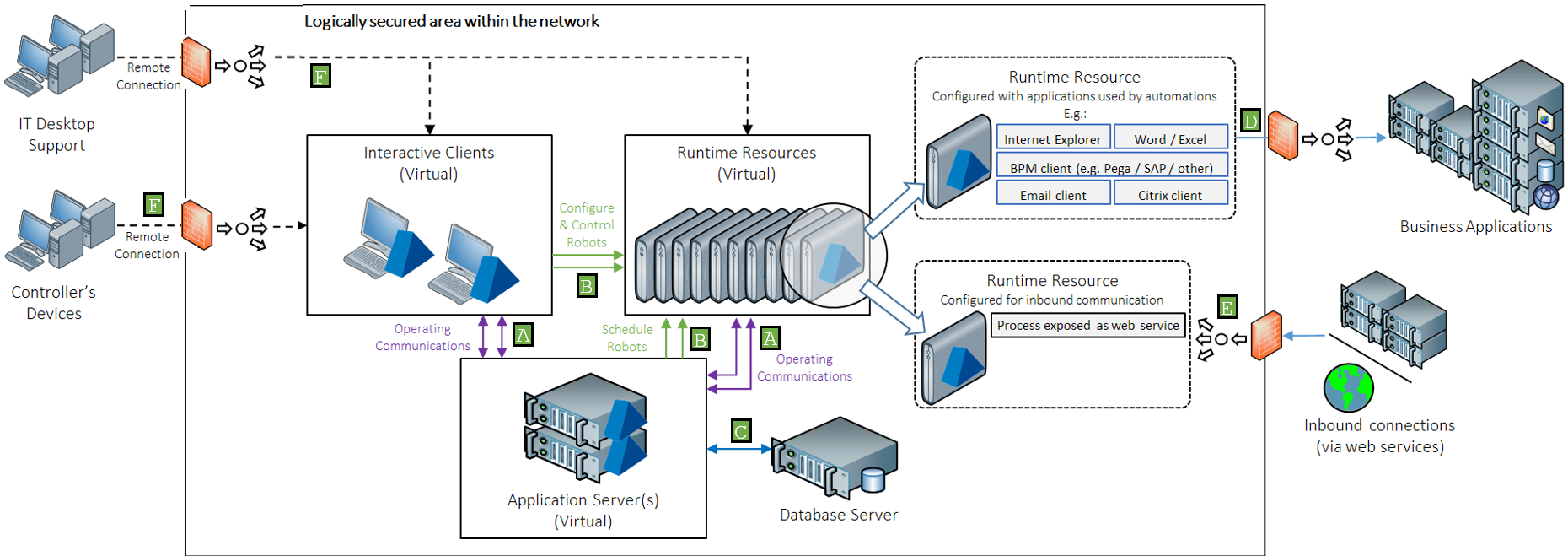
This guide enables architects and system implementers to understand how to secure the network connectivity associated with Blue Prism. The diagram provides an overview of the common communication that occurs with the Blue Prism platform.
This guide provides details of how to configure Blue Prism in a secure enterprise environment. However, it is advised that you also consult the Robotic Operating Model (ROM) Security information on the Blue Prism Portal for recommendations of best practice.
|
Communication |
Description |
Encryption options |
|
|---|---|---|---|
|
Blue Prism connections to application server |
A |
Primary communication stream for the devices to send data to, and receive data from the database (via the application server). |
Natively encrypted by default when all Blue Prism components are deployed within an Active Directory network infrastructure. |
|
Instructional connection to runtime resources |
B E |
Instructions received by runtime resources. For example, to start/stop processing; or to provide a status update. |
Certificate-based encryption can be applied by manually deploying an appropriate certificate to each runtime resource and updating the device start-up parameters. |
|
Blue Prism database connection |
C |
The read/write connection between the application server and database. |
Certificate-based encryption can be applied to the connection by leveraging SQL Server functionality which can auto-generate self-signed certificates or leverage an existing verifiable certificate. |
|
Runtime resources connecting to target applications |
D |
Runtime resources interact with business applications as part of process automations. |
Dependent on the security provided by each respective third-party target application based on the nature of each connection. |
|
Remote connectivity |
F |
Users controlling the platform commonly use a remote connectivity tool to access centrally deployed devices. |
Leverages the security provided by the respective third-party remote connectivity tool. |
Blue Prism network security
To strengthen Blue Prism network security, role-based access control (RBAC) should be utilized and only specific users, such as infrastructure administrators, should be granted access to application servers and network communication configuration. All other users should be denied access by default. Explicit allow/deny access should be configured for all users and the principle of ‘Least Privilege’ followed.
These controls should also extend to the users of Blue Prism, so that only those who need access to the platform are allowed and are only given the level of authority required to carry out their role, while all others are denied access by default.
It is advised that you also consult the Robotic Operating Model (ROM) Security information on the Blue Prism Portal for recommendations of best practice.
 Docs
Docs